What Is Employee Monitoring Software?
Maybe you’re an employee that thinks your employer is monitoring you at work and you’re not sure how they can do that. Or, perhaps you are a business owner managing a small team and you’re not quite sure your employees are working as hard as they say they are.
In either case, you’re wondering what employee monitoring software is, what it is capable of, and how it can potentially improve your workplace.
Industry professionals agree that employee monitoring software can drastically improve your workplace productivity and help to minimize the chance of an insider threat. Employers are also allowed to exhibit some form of employee monitoring while employees are on the clock, so long as they are mindful of employees’ privacy rights.

What is Employee Monitoring Software?
Employee monitoring software is a piece of software that can be downloaded onto a computer for the purposes of monitoring that computer and the actions of its user(s). Typically, this software will be downloaded on any work computer or employee computer overtly or in secret.
Using the main admin terminal, the software can then access the data collected on each monitored computer to oversee employee behaviors.
Employee monitoring software for terminal servers or workstations will have surveillance features to monitor employee behaviors for insider threats, as well as time-tracking features to be used as an attendance software. The software will also have features that allow managers to monitor the progress of a big project or small day-to-day tasks.
Reasons Why an Employer Might Need Employee Monitoring Software
It is extremely normal for an employer to want to verify that their employees are doing the work that they say they are. They also need to monitor their computer networks to ensure optimal cybersecurity. Employee monitoring software can assist in both of these matters.
Employee monitoring software is a powerful tool that can be used for monitoring the productivity levels of both in-house and remote employees so that project and team managers can monitor team and employee performance to estimate and manage timelines. It can also be used to improve employee organizational skills if an employee seems to be struggling with time management.
Employee monitoring software can be used as an added defense against these insider threats because it can perform activity monitoring on each computer, determine the baseline or normal user behaviors, and then alert team management when certain behaviors that are considered risky are observed.
Remote employee monitoring can be difficult since remote employees might use their own computer and can get away with not working while on the clock since they are not being surveilled. That is why computer monitoring is the perfect option for companies who are not physically around a remote team and need to do employee tracking for productivity as well as threat monitoring.
Depending on the software used, remote employee monitoring can be conducted secretly as installation can happen through remote access is given. If the employer does not have access to secretly install the software as an administrator, then the remote employee will need to install it themself.
Features Included in Employee Monitoring Software
Employee monitoring software can be purchased solely as a time tracker or to monitor both time and insider threats. If you are currently shopping around, we recommend a software that can do both. No matter what, make sure that you get the software that suits the needs of your business.
Here we break down the features that are available in employee monitoring software for each purpose:
Employee productivity tracking features
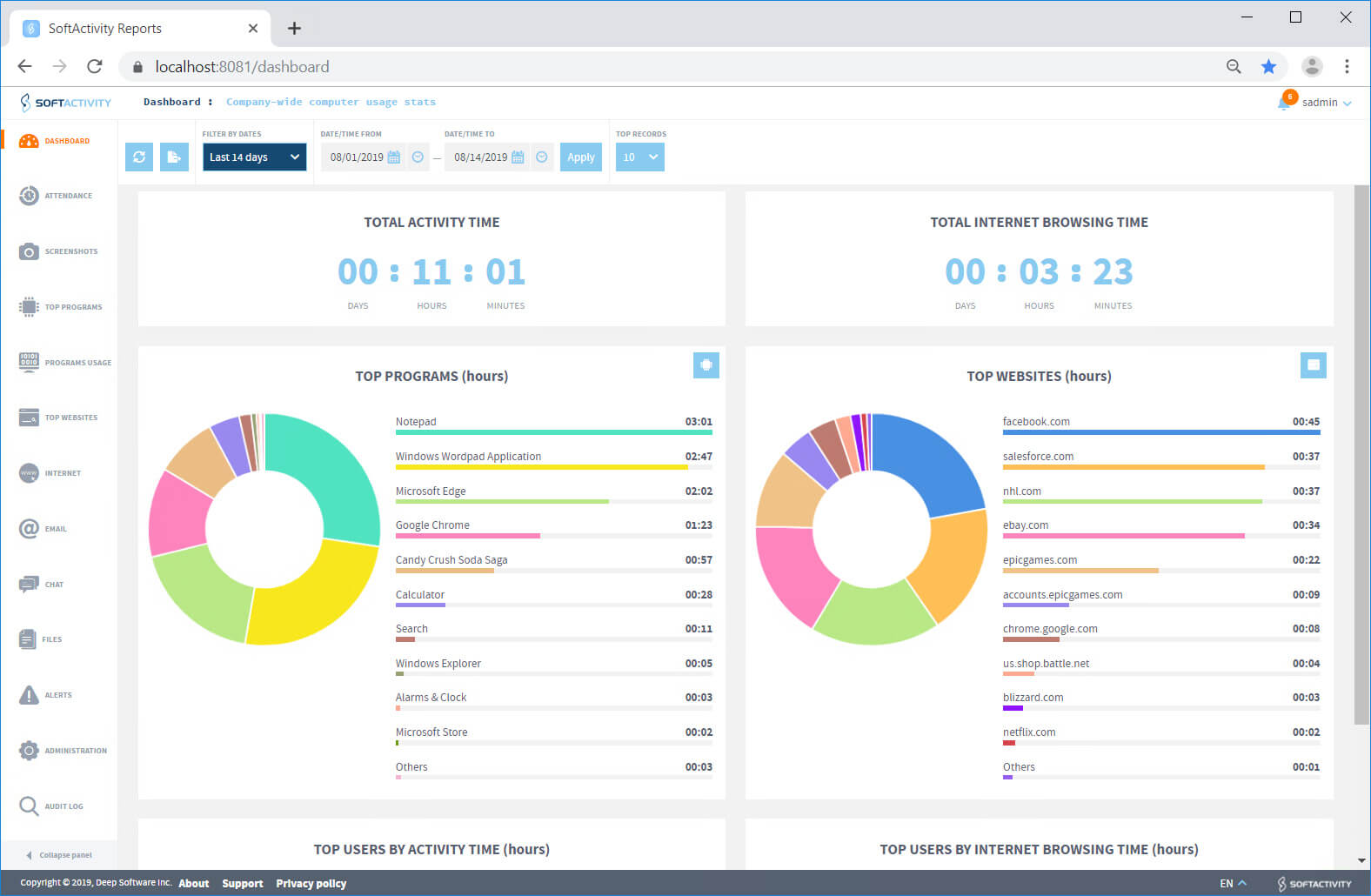
When monitoring for productivity, you need tools that will track the time spent on tasks and projects, track the websites that employees visit, and report how employee time is conducted during work hours.
Here is a list of employee productivity tracking features that are usually included in employee monitoring software:
- Time tracking for an individual, team, and non-project based task
- Time spent on websites and apps
- Hours spent working while time is being recorded
- Employee performance metrics reports
- Website restrictions
- Easy-to-read dashboard
- App for tracking on-the-go
- Time wasted reports and social media tracking
- Clear individual timesheet report
- Remote worker monitoring
- Project and task estimations
- Billable hours versus working hours
- Idle detection
If your business operates with a remote employee, you may want to adopt monitoring software as this is the only way to truly know that your employees are working for you rather than against you.
By adopting a monitoring solution for productivity, your team managers can do less micromanaging and instead work with your employees to develop clear productivity reports and data. Collecting worker productivity data will alert management to potential drops in employee efficiency. With this data, teams can create productivity plans and use proper management techniques to boost employee engagement.
Employee and insider threat monitoring features
The thought of monitoring an insider threat almost seems nefarious. However, the bottom line is that every company has some type of valuable asset that can be stolen from the company or used as a form of blackmail.
In any case, if you are collecting sensitive information from clients, like payment information, and hackers or malicious actors have a way of obtaining this information, then they will try to do so. You are obligated to protect company, employee, and client data by using a secure firewall, secured network, HTTPS connection, encryption for data storage, and multi-factor authentication.
In addition to these workplace and video surveillance techniques, companies should adopt certain forms of monitoring for employee computer activity. If you are looking for an employee monitoring solution that can do both time track and monitor insider threats, be on the lookout for these surveillance features:
- Monitoring all computer activity during a certain session
- User behavior analytics to establish baseline employee activity
- Keystroke logging
- Logging electronic communication
- Restricted access and data transfers
- Alerting a team member when a security threat is infringed upon
- Tracking internet usage
- GPS tracking via a mobile app
- Website restrictions
- Remote monitoring
- Stealth installation
It is very important that if you are monitoring your employees for insider threats, that you do not tell them that you are doing so. It should be used in conjunction with a strong cybersecurity protocol.
If you are using the program for time tracking, you can tell the employees that time tracking is needed so that they clock in and track for projects when they are in progress. However, you do not want to inform your employees that you are suspicious of their computer activity as they might have trouble trusting you.
Additionally, by giving them this information, you are giving them insider information on how to work around a surveillance software.
Employee Privacy Rights When Using Monitoring Software

When an employee agrees to work for a company, they are, to a certain extent, also agreeing to some level of workplace monitoring. And in many cases, workplaces are required to place these protections in place. In July of 2019, over 100 million people were affected by a data breach of credit card and banking company Capital One. And while it might seem obvious that a financial institution would need high-end employee monitoring and security, businesses every day handle the personal information of customers and this data can be used in a malicious way.
Employee monitoring might come in the form of monitoring at a physical office and being recorded on video for security purposes. Other forms of monitoring include keycard entries, phone recordings, and computer recording.
Monitoring software that is downloaded onto a user computer for the purposes of monitoring employee behavior will capture a lot of data about employees. Therefore, it is up to the admin or employer to configure the settings so that employee privacy and security is optimized. For example, if the monitoring software records the computer screen live, you’ll want to adjust the settings so that passwords and private information is not captured in the feed. The same settings can be set for screenshot images captured by the software.
If the software that your company uses has a keylogger in it, that keylogger might also record personal information, like credit card numbers and passwords. It is not reasonable to ask your employees not to type this information. It is also not reasonable to fully trust the software company you are using to record this information with encryption (although this absolutely should be the case!). Make sure that the keystroke logger in the software does not record this private information or that it redacts it immediately.
As an employer who is adopting employee monitoring, it is up to you to ensure that the user activity data that your company collects is collected and stored securely. Make sure that the software company you choose offers database backup and that it keeps all data password protected and encrypted.
Employee monitoring software is usually integrated into an employee monitoring system and a cybersecurity system, so be sure to consult your team’s IT department before you purchase employee monitoring software.
Purchasing Employee Monitoring Software for Your Company
When looking for an employee computer monitoring software for your company, consider an employee monitoring tool that has more than enough capability for your team’s needs. Because monitoring software is multi-useful, be sure to find a comprehensive program that can track time and attendance, track project and task times, and supply administrators with time wasted reports.
Since there are many simple time tracking tools out there, you shouldn’t waste your money on a piece of software that is a “big” time tracking tool.
Instead, opt for a monitoring tool that can operate as a time tracking tool but also monitor your employees to protect against insider threats. Software that includes user behavior analytics (UBA) can do just that, and it can keep your company one step ahead of rogue employees or malicious attackers.
By SoftActivity Team