With a plethora of live and digital options competing to entice workers’ eyes and minds away from their jobs, more and more companies are choosing to install tracking on workers’ computers. Not only that, but companies are finding that their data is increasingly susceptible to targeted, malicious attacks.
Employers can mitigate these risks by implementing a monitoring strategy. A monitoring strategy usually involves a comprehensive employee monitoring system. With a monitoring tool in place, organizations can noticeably boost employee productivity, reduce business risk, improve the quality of work, enhance security, prevent data leakage, and protect intellectual property.
If you’re considering monitoring employee activity but you’re unsure where to start or have concerns over employee privacy, then you’re in the right place.
This expert guide will walk you through everything you need to know about employee monitoring, including:
- What employee monitoring is and why it’s popular
- The business use case for monitoring
- Employee perspectives
- Considering remote work
- Legal aspects
- A checklist for choosing a monitoring system
- Step-by-step guide to building a monitoring solution
- Best practices for employing a system
- Which software is right for you
Let’s dive in!
What is Employee Monitoring?
Employee monitoring is broadly defined as a way for employers to observe and track employee activity. This can include all user activity when accessing a corporate network, remote worker activity, or when representing the company outside of the office.
The main purpose of employee monitoring is to collect data on user activity and to monitor certain types of employee behavior, or behavior on the network, that can either put your company at risk or be detrimental to your bottom line.
Employee monitoring can be accomplished in a number of ways. It is usually a part of a larger monitoring system, sometimes referred to as an Enterprise Management Systems (EMS), which is made up of several types of tracking or surveillance.
Monitoring within an EMS may include:
- ID badges that use bar-codes, magnetic stripes, proximity, smart credential, or radio-frequency identification (RFID) technologies to track and manage workers and assets. It can also be used for time tracking.
- Closed-circuit video cameras for workplace surveillance, including video surveillance systems that record employee activities that can be searched by event, activity, time, and date.
- Employee monitoring software allows employers to observe and track computer usage, including email messages written and received, other electronic communications, applications use habits, individual keystrokes, Internet browsing history, network logon/off times, files copied to USB drives, and their physical location (for remote workers).
- Onsite security staff serving to deter unauthorized access to buildings or equipment, and employee mischief or theft.
- Biometric facial-recognition systems that utilize cameras and AI (Artificial Intelligence) to confirm identity by comparing facial textures and shapes with databases using photos or video frames.
- Phone tapping (phone calls recording) can be used to establish facts around team members’ productivity, quality of customer service, and provide documentation in cases where leaks of confidential information and/or trade secrets may be a concern.
- Location tracking uses GPS or RFID technology in company-issued phones to identify workers’ locations and movements. GPS tracking can also be used for fleet vehicle tracking.
- Private investigators are sometimes engaged by organizations wanting to monitor staff meetings outside of the office (in cafes, coffee shops, etc.) in circumstances in which there is suspicion about information leaks.
- Social media tracking includes automatic scanning and analysis of social media posts by employees to make sure they adhere to the company’s policies
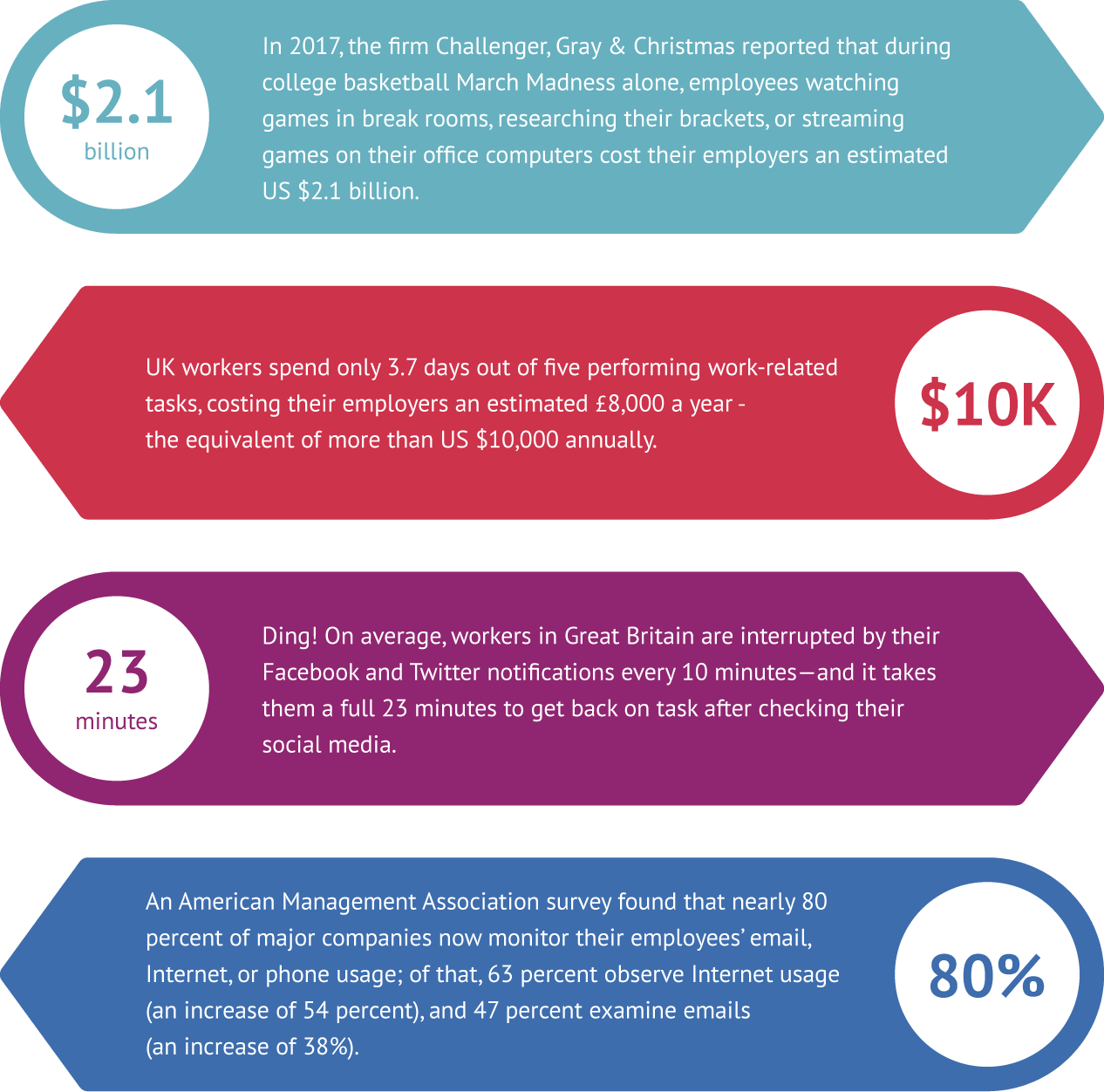
Growth in monitoring usage
The increasing popularity of computer monitoring can be most clearly understood by examining some key data associated with the productivity issues and financial impact of a distributed or distracted workers:
Sources:
https://www.marketplace.org
http://workplaceinsight.net
https://www.sciencedaily.com
https://abcnews.go.com
The business case for user monitoring

It’s been estimated that the employees in the top 20 percent in performance make 80 percent of an organization’s success happen. Imagine what could be accomplished if there were an efficient way to boost employee performance for the remaining 80 percent?
Additionally, according to Global Workplace Analytics, businesses lose around $600 billion a year due to workplace distractions. These figures improved when workers were working remotely. For example, American Express found that their remote workers produced 43% more than those in the office. This is common. Two-thirds of employers reported that their remote employees were more productive.
- Improved productivity – keeps more employees on-task, and for longer periods of time
- Protection of intellectual property – assures those intangible assets stay within the control of your company
- Decreased business risk – easier detection of malicious or careless employee activities that can threaten a business
- Enhanced compliance – better data to establish and demonstrate adherence to industry standards and legal requirements
With more and more employers becoming concerned with the sharply increasing threats to security and productivity, the business value that can be realized by overseeing users’ activity is apparent.
How workers feel about monitoring: What you need to know

Employees generally have a range of strong reactions to the thought of having their actions monitored in the workplace. Many are concerned about their right to privacy, and how that extends into their professional environment. Some feel that employee tracking fosters a Big Brother culture of fear and suspicion.
And those feelings are, of course, valid. There was widespread outrage when companies began to announce that they would be implanting RFID chips in employees’ hands. These chips would be scanned to automate and automatically track activities like entering buildings, making cafeteria purchases, and logging into corporate networks.
There were suggestions that employers could use these chips to track employee activities outside of working hours, and that workers’ privacy and personal data could be compromised.
Once put into practice, however, many employees reported that the chips were easy to use, and made their days run more smoothly. In fact, user adoption increased.
It is important to note that with proper communication, employee monitoring software can be implemented without compromising workplace culture.
When considering remote work
The workplace is changing rapidly. More companies are rolling out remote work programs. With remote workers, user activity monitoring is far more critical. This is because, with any remote employee, you are limited in the ways that you can observe and control their work-related activity.
You should adopt a remote employee monitoring tool for the following reasons:
Cybersecurity: A remote employee will most likely be working from a personal or public network, which can be more easily compromised. Monitoring remote connections can also boost the security of your sensitive data.
Productivity: While productivity is reported to be higher for remote workers, it can also be the case that employees slack off and choose to watch TV instead of work. With regular time tracking, your employees know what you expect from them in terms of productivity.
Employee morale: Remote employees can sometimes feel ostracized. Monitoring activities do not have to always be investigative. Create a company culture built around productivity and connectivity through powerful monitoring software productivity apps.
If your company is considering a remote workforce, a tracking tool will ensure that employees are working while on work time, that their remote computer is safe against a potential data breach, and to monitor user behavior when employees need remote access to sensitive information.
If you’d like a remote monitoring tool, look for the following features:
- Remote access control and install
- Timesheet tracking
- Task management
- Virtual desktop support
- App monitoring
- Video or computer image monitoring
- Keystroke logging
- Bandwidth trackers
- Support of terminal services
- And reports on poor time use
Additionally, many monitoring tools are naturally supportive of monitoring a distributed team. This means that you don’t need to get any special monitoring software in order to manage a remote team. Monitoring tools can be deployed onto a computer remotely and can optimize an employee’s computer for security.
Remote employee monitoring does come without legal risk, which is why an employee monitoring program needs to be scalable and controllable.
The legal aspects of employee monitoring

Federal laws and state privacy laws in the USA generally allow an employer a great deal of leeway in defining the extent of their monitoring programs. Some state and local laws require employee consent, yet most don’t require companies to inform staff members they are being monitored at all.
When specifically talking about electronic monitoring, some states, including Connecticut and Delaware, prohibit an employer from monitoring workers without prior notice. The federal Electronic Communications Privacy Act (ECPA) supports two cases for monitoring employees:
- Legitimate business purpose – this allows companies to monitor employees’ electronic communications if it has a “legitimate business purpose” for monitoring
- Prior employee consent – an employer also may monitor workplace communications if they have obtained prior employee consent ― usually done during the onboarding process as part of standard paperwork completed on the first day
Even with consent, however, litigation can still occur. Today, most worker-initiated monitoring-related lawsuits are associated with terminations due to misuse of company-owned cars and smartphones. As tracking technologies continue to develop though, there may be a rise in litigation around employers’ use of advanced technologies such as drones or other yet-to-be-developed devices.
How employers can protect themselves from a legal standpoint
Tom Wulffson, a partner at the law firm Carothers DiSante & Freudenberger in California, represents companies in employee privacy cases. He recommends that companies follow these guidelines to ensure that they are on the right side of employee privacy:
- Always disclose any surveillance to your team members
- Define a legitimate business interest for monitoring
- Do a cost-benefit analysis comparing the GPS tracking of company-provided smartphones with the data you expect to yield by tracking that device
- Ensure that all tracking is consistent across all employees and that it’s carried out by trained and trusted staff or third-party vendors
The takeaway? When implementing a tracking program for your company, it’s always best to research applicable legal issues in your area and get workers’ consent whenever required by law.
CHECKLIST: How to choose a monitoring solution for your business

Identify the problems you want to solve
Every business is different, and a one-size-fits-all monitoring solution won’t work. Make sure you understand what your supervision strategy needs to address, so you can find the best match:
- Lagging productivity
- Intellectual property theft
- Behaviors creating business risk
- Inaccurate or not enough data collected for compliance reporting
- Inefficient new hire onboarding
- Staff oversight and management challenges
- Automate manual HR/Payroll processes
- Insider threats
Outline your business requirements
From industry regulatory issues to federal, state/province, and local laws, identify the business requirements specific to your company:
- Health Insurance Portability & Accountability Act (HIPAA) – healthcare industry data privacy and security provisions
- Sarbanes-Oxley (SOX) – US federal law outlining requirements for all US public company boards, management, and public accounting firms
- Payment Card Industry Data Security Standard (PCI DSS) – information security standard related to the processing of major credit cards
- General Data Protection Regulation (GDPR) – data privacy regulation for the European Union that standardizes data protection law and imposes strict new rules on controlling and processing personal data
- Human Resources – your HR leadership should have early and extensive input into solution development to ensure minimal impact on morale, and help drive internal support for the solution
- Industry requirements – every employee tracking solution will look and perform differently based upon the industry in which it’s being used; ensure that the elements of your solution are all appropriate for your specific case and business model
- Remote workers – organizations with a distributed workforce may need to focus their supervision primarily on networked and mobile device
Monitoring technologies for your business model
Most monitoring solutions are made up of multiple elements, tailored to the specific needs of an organization:
- ID badges
- Closed-circuit video cameras
- Computer surveillance software
- Onsite security staff
- Biometric facial-recognition systems
- Phone tapping
- Location tracking (GPS)
- Other
Different types of functionality
All software monitoring solutions are not created equal — define the features and functionality that will provide the most meaningful return on investment:
- Real-time viewing
- Reporting
- Simultaneous computer/user views
- Alerts for specific content, user behavior, or policy violations
- Email and Instant messaging tracking
- Usage data on laptops traveling with remote workers
- Staff attendance tracking
- Website tracking (Internet usage monitor)
- Apps usage
- Keystroke logger (or keylogger)
- Screen supervision and scheduled screenshot captures
Step-by-step: How to build an employee monitoring solution specification

Once you’ve decided what you require from a solution for overseeing workers activity, consolidate the information you’ve gathered into a master roadmap that will guide you through purchase and implementation.
What goes into a solution specification? There’s no “one-size-fits-all” here, but your solution spec will likely include some or all of the following:
- An Executive Summary that provides background information and an overview on the project
- A list of assumptions, risks, and dependencies that will impact the project
- Detailed functional requirements to outline any criteria that will be used in solution design and testing
- A reference list of supporting documents, and links to relevant resources
- Revision log to track changes, and document responsibility for updates
- A glossary of both technical and non-technical terminology used in the spec
Best practices for deploying an employee tracking solution

Implementing a solution for tracking employees at work can be helpful in resolving productivity, security, and insider threat issues for any size company. To streamline the transition throughout your organization, look to the following set of core best practices:
Introduce the solution to leadership teams and get buy-in on business value
As with any new initiative rollout, it’s essential to get key leadership on board with the solution early on to help drive understanding and adoption throughout the company. Once a decision has been made regarding the nature of the solution you’ll be implementing, brief your executive team and management leadership to help them understand the issues that the solution will resolve, and the business value that will be realized from monitoring.
Develop a Computer Use Policy and have all employees sign it
Getting a signed computer use policy from all workers will ensure that there is a company-wide understanding of expectations around the use of company-owned hardware, software, and network infrastructure. A basic computer use policy should include the following:
- General usage – the basic ground rules of your computer policy, such as sending/receiving content, adult content, and personal content
- Monitoring – an outline of how voice and data communications may be monitored
- Security – an overview of expectations around confidentiality and user identity
- Networks – network and Internet usage policies for workers as representatives of the company
- Copyright – guidelines for proper use of copyrighted materials belonging to the company — and to third parties
- Discipline – corrective actions that may be employed for those in violation of the computer use policy
Need help putting together your policy document? Download our free Computer Use Policy Template and customize it to your need.
Train managers on new processes and software
Once the solution is in place, start to work with your Human Resources and IT departments. Train management teams on processes and tools associated Once the solution is in place, start to work with your Human Resources and IT departments. Train management teams on processes and tools associated with your employee auditing initiative. If you worked with a partner company to deploy computer monitoring software, arrange to have their sales engineer conduct training on how to use the new system, and how the reporting process works.
Have managers introduce the solution to their teams to drive awareness, share employee benefits, and address concerns
It’s important to give management the information and tools they’ll need to successfully introduce the initiative to the employees on their teams. Consider developing a slide presentation or brief video for them to share that will explain the employee-facing value of monitoring. Managers can explain that it is not used for spying on them, but to improve overall security in the company.
Depending upon the organization, benefits for the team members may include:
- Improved workplace safety (no access for unauthorized individuals)
- Less opportunity for theft of personal belongings
- Time savings (quicker and easier authorization to enter the building, log into the network, etc.)
- Insight to help you improve your productivity
- Helps managers encourage better work-life balance through network use logs
If an employee has a better idea of how workplace activity supervision can help benefit both themselves and the company as a whole, then they are more likely to warm up to the idea of being monitored while they work.
Roll appropriate parts of the solution out in phases across the company
If you’re implementing user monitoring in an enterprise environment, it’s recommended to stage the rollout of certain components to prevent work slowdowns due to learning curves. It also enables you to receive incremental feedback from managers and staff, and make necessary adjustments and improvements prior to introducing the solution to the next group within the company.
Provide ample, responsive support for users to troubleshoot and resolve issues
Make sure that there is a clear path for both staff and employee communications, especially for those who have questions about your employee monitoring initiative. These issues can range from privacy concerns to system troubleshooting. Make sure to identify which members of the leadership team are on point to respond to each type of inquiry.
Gather feedback from managers and employees to help improve the experience
For the first 9-12 months, schedule regular check-ins with managers to gather feedback and work on strategies to address concerns as they arise. Gathering internal input early and often is key to having the smoothest implementation possible, but there will always need to be adjustments, so keep the lines of communication open to your teams.
Boost productivity & protect your business

If you need an easy-to-use software solution to support your computer monitoring initiative, SoftActivity can help you boost productivity and protect your business assets.
SoftActivity Monitor is a tool that can:
- Discourage the personal use of company networks for web surfing, instant messaging, private emails, and social media
- Eliminate time wasted on games and unproductive videos
- Contribute documentation around instances of harassment
- Protect against workplace fraud
- Provide documentation for disciplinary action
- Prevent theft or misuse of intellectual property and trade secrets
- Maintain records of electronic communications to improve compliance
Find out how SoftActivity can help you protect your business and boost productivity. Download a free trial today!
About SoftActivity
SoftActivity is a leader in employee monitoring software, with thousands of customers worldwide. Our employee monitoring tools protect organizations from business risks like insider threats and office cyberloafing. SoftActivity provides keystroke logging, Internet and apps usage history, attendance tracking, screen recording, real time alerts, reports and other user monitoring technology.
Related:
- The 10 Most Common Questions Employees Have About Computer Monitoring
- How To Create a Productivity Plan Using Employee Monitoring Software
- The Benefits and Pitfalls of Deploying Employee Monitoring Software
- Insider threats guide
- Using Employee Monitoring to Boost Productivity
- Computer Use Policy Template – use to inform employees and collect formal consent to monitoring
- What to Look For in Employee Monitoring Software
- How to Keep Employees Focused and Productive
- How to Apply Employee Monitoring Without Compromising Workplace Culture
- 7 Reasons Why You Need Employee Monitoring Software for Your Remote Team
- What Is Employee Monitoring Software?
- Is using employee monitoring software a good idea?
FAQ – Employee Monitoring
Q: What is employee monitoring?
Employee monitoring is broadly defined as a way for employers to observe and track employee activity while in the workplace, when accessing the corporate network, or when representing their company outside of the office. Read more here: What Is Employee Monitoring Software?
Q: What problems does employee monitoring solve?
Employee monitoring can help improve productivity, prevent intellectual property theft, reduce the behaviors that create business risk, enhance compliance reporting and auditing, streamline new hire onboarding, eliminate staff management challenges, and make manual HR and payroll processes more efficient by tracking attendance and work hours.
Q: What are the challenges of rolling out a user monitoring initiative?
You’ll be dealing with the cost and time involved in installing and learning new systems, leadership that may be resistant to dramatic change, HR professionals trying to adapt their guidelines to the new expectations, and employees concerned about their privacy in the workplace.
Q: Is it legal to monitor my employees’ workplace activities?
Federal and state privacy laws in the US generally allows an employer a great deal of leeway to define the extent of their employee activity tracking programs. Some state and local laws require employee consent, yet others do not require companies to inform workers they are being monitored. Make sure to familiarize yourself with privacy laws that apply in your location.
Q: Do I have to tell my employees that I’m monitoring their activities?
Some states, including Connecticut and Delaware, prohibit an employer from user or workplace monitoring prior notice. The federal Electronic Communications Privacy Act (ECPA) supports two cases for monitoring workers: When there is a “legitimate business purpose” for monitoring, and when prior employee consent has been obtained. In implementing an user tracking program for your company, it’s always best to research how the privacy laws in your area apply and get employee consent whenever required.
By SoftActivity Team